EIMS Relay Security
How does EIMS 3.2 decide if a message should be relayed?
EIMS 3.2 relay security
EIMS 3.2 SMTP Submit
How does EIMS 2.1 to 3.1 decide if a message should be relayed?
EIMS 2.1 to 3.1 relay security
How do I secure my EIMS Server version 2.1 to 3.1 against relaying?
What to do if you can't secure your server immediately
Such and such site says EIMS can't be secured against relaying.
What is relaying?
Relaying is when a mail server accepts and delivers a message to another server.
A mail server accepting and delivering a message to an account on that server is not relaying. A server accepting a message for an account that forwards to an address on another server is also not relaying.
When the protocol for email (SMTP) was originally designed, relaying wasn't a security issue so no relay security was built in. Unfortunately spammers came along and changed all that by abusing the relaying capabilities of mail servers, so now it is necessary to restrict relaying to avoid your server being hijacked.
A number of different ways of restricting relaying have been added on to SMTP. EIMS supports two ways of restricting relay, domain and IP based restrictions, and SMTP AUTH.
Domain and IP based restrictions decide if a message should be relayed based on either the domain of the recipient address, or the domain of the sender address and the IP address of the client. The main advantage of this method is that it can support existing clients as is. The main disadvantage is that it is not very useful for supporting roaming clients that are connecting from unknown IP addresses.
SMTP AUTH (also known as SMTP Authentication or SMTP Authorization) is the ideal solution for roaming clients, as the client can authenticate with a username and password to allow relaying. This requires support for SMTP AUTH in the client (now days all clients support SMTP AUTH) and it typically needs to be turned on by the user. EIMS version 2.1 and later support SMTP AUTH with CRAM-MD5, version 3.0 and later also support SMTP AUTH with PLAIN and LOGIN, version 3.1 and later also support SMTP AUTH with NTLM.
Some email servers support POP-before-SMTP, where they will allow relaying from an IP address if a client has checked mail from that IP address in the last few minutes. There are a number of disadvantages to this, it requires that the client connect before sending (most clients don't support doing this automatically), it leaves a window where the IP address the client used could potentially be hijacked by someone else, and for clients behind routers or dialup servers using NAT it allows relaying for everyone else behind the router or dialup server. EIMS has never supported POP-before-SMTP and I have no plans for supporting it, SMTP AUTH has always been a more secure and standards based way of achieving the same results.
EIMS 1.3 and 2.0 supported restricting relaying by domain name only, however that still allowed anyone to relay if they forged an allowed domain. Users of these old versions should upgrade.
How does EIMS 3.2 decide if a message should be relayed?
EIMS 3.2 will relay a message if it meets one of the following criteria:
- The client has authenticated with SMTP AUTH
- The domain of the recipient address is in the list of backup MX domains
- The domain of the sender address and the IP address of the client match an entry in the Relay Security, and for sender addresses in a local domain the address must have Login Enabled turned on.
EIMS 3.2 relay security
New installations of EIMS 3.2 default to being compeletely secure.
If you have upgraded from an older version of EIMS that was not secured,
you will need to remove entries from the Relay Security that allow relaying from untrusted IP ranges.
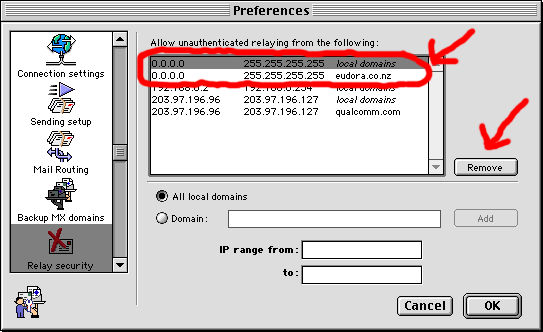
Clients connecting from untrusted IP ranges should turn on SMTP AUTH in their mail client.
To make sure you don't turn your server in to an open relay:
- Do not configure the Relay Security settings to allow access from untrusted IP ranges.
- Do not allow the IP addresses of insecure servers in the Relay Security settings, your server could end up as part of a multi-hop open relay.
- Do not add an entry for "*" in the Backup MX domains settings.
- Make sure all accounts with Login Enabled turned on have a non-trivial password. If someone can guess the password for an account, they can use SMTP AUTH to relay mail.
EIMS 3.2 SMTP Submit
In order to prevent spammers from using dialup accounts to send spam through other servers, many ISPs are blocking access from dialup clients to SMTP (port 25) other than to that ISPs SMTP server. As a result, roaming clients that connect via these ISPs typically have to reconfigure their client to use that ISPs server. EIMS 3.2 supports a solution to this problem called SMTP Submit, where it can also receive mail on a second SMTP port, port 587 by default. If your users configure their client to use port 587, then they don't need to change any configuration when connecting from other ISPs.
Using the SMTP Submit port also makes it easier to manage client to server SMTP load vs server to server SMTP load. If all your clients are switched to port 587, then any sort of overloading on port 25, due to large incoming mail volumes or DoS (Denial of Service) attacks, will not interrupt sending mail for clients.
How does EIMS 2.1 to 3.1 decide if a message should be relayed?
EIMS 2.1 to 3.1 will relay a message if it meets one of the following criteria:
- The client has authenticated with SMTP AUTH
- If the Relay Restrictions are set to the 1st option EIMS will relay if:
- The domain of the sender address is a local domain or not listed in the Relay Restrictions and the IP address of the client is allowed (or not denied) in the IP Range Restrictions for Mail Relay.
- If the Relay Restrictions are set to the 2nd option EIMS will relay if:
- The domain of the recipient address is in the Relay Restrictions list.
- The domain of the sender address is a local domain or in the Relay Restrictions list and the IP address of the client is allowed (or not denied) in the IP Range Restrictions for Mail Relay, and for sender addresses in a local domain the address must have Login Enabled turned on.
- If the Relay Restrictions are set to the 3nd option EIMS will relay if:
- The domain of the recipient address is in the Relay Restrictions list.
- The domain of the sender address is a local domain or in the Relay Restrictions list.
- the IP address of the client is allowed (or not denied) in the IP Range Restrictions for Mail Relay.
EIMS 2.1 to 3.1 relay security
New installations of EIMS 3.1.1 to 3.1.5 default to being compeletely secure. See below for instructions on securing older installations.
To make sure you don't turn your server in to an open relay:
- Do not configure the IP Range Restrictions for Mail Relay to allow access from untrusted IP ranges.
- Do not allow the IP addresses of insecure servers in the IP Range Restrictions for Mail Relay, your server could end up as part of a multi-hop open relay.
- Do not use the 3rd option in the Relay Restrictions.
- Do not add an entry for "*" to the Relay Restrictions.
- Make sure all accounts with Login Enabled turned on have a non-trivial password. If someone can guess the password for an account, they can use SMTP AUTH to relay mail.
If you need to do something like relay mail for a web server while still having your EIMS server act as a backup MX for other domains, EIMS 3.2 has relay security that offers better flexability and security for this sort of thing, you should upgrade.
How do I secure my EIMS Server version 2.1 to 3.1 against relaying?
Set the Relay restrictions to the 2nd option and then set the IP Range Restrictions for Mail Relay to only allow access from your local network and/or any trusted IP ranges.
Clients connecting from outside these IP ranges should turn on SMTP Authentication in their mail client.
Follow these steps to configure your EIMS Server:
- Connect to your server using EIMS Admin.
- Open the preferences window by selecting Preferences from the Admin menu.
- Click on the Relay Restrictions icon.
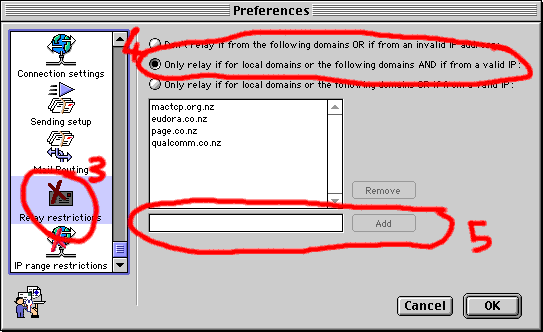
- Click the button for Only route for local domains or the following domains AND if from a valid IP:.
- Enter in any domains that should be allowed to relay through your mail server.
- Scroll down in the list of icons and click on the IP Range Restrictions icon.
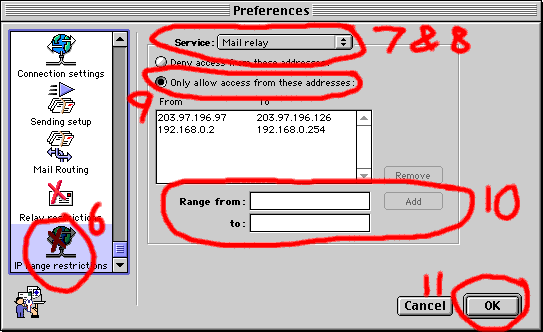
- Change the Service popup menu to Mail Relay.
- Double check that you have changed the Service popup menu to Mail Relay, a lot of people miss this step or get it wrong. Do not set the IP Range Restrictions for SMTP like this, that will typically block all mail from the outside world.
- Click on the button for Only allow access from these addresses:
- Add your local IP range and/or any other trusted IP ranges that
- Click on the OK button.
Clients connecting from outside these IP ranges can relay if they turn on SMTP AUTH in the mail client.
What to do if you can't secure your server immediately
If you can't secure your server immediately, due to large numbers of clients connecting from untrusted IP ranges that need to turn on SMTP AUTH, there are some options for increasing relay security to block spammers and get off blacklists.
With EIMS 3.0 and later you can turn off Login Enabled for accounts to stop them being used to relay. Many blacklists will test your postmaster account to see if it can relay, turning off Login Enabled for the postmaster account will often get you off the blacklist. This should only be considered to be a temporary measure while you finish securing your server, as any other account with Login Enabled turned on can be used to relay until you have secured your server using the IP Range Restrictions for Mail Relay.
In order not to block all of your clients at once, you can start progressively blocking IP ranges in the IP Range Restrictions for Mail Relay. To get a good idea of what IP ranges your clients are connecting from, export a list of users from EIMS Admin (open the domain and go to Export Users from the Users & Groups menu) and sort the list by IP address. You should then be able to identify large IP ranges that clients do not connect from, as well as get an idea of how many users will be blocked in a particular IP range so you can block a few users at a time and have them turn on SMTP AUTH in their mail client.
Such and such site says EIMS can't be secured against relaying.
Such and such site is very out of date (and if it is the site I am thinking of, they have repeatedly ignored requests to update their web page with current information), I suggest you ignore it. EIMS 2.1 (which was released in April 1998) and later can be completely secured using the above procedure.
EIMS 2 users can download free updates to EIMS 2.2.2 from Qualcomm.

Questions?
Features
Demo
Support
EIMS Quick Start
Email client configuration
EIMS 3.3 Documentation
Relay Security
OS 9 to OS X
Updates
EIMS mailing lists
Filters
Last modified 28 October 2022. Copyright 1997-2022 Glenn Anderson.