EIMS 3.3 Documentation
The SMTP Host List
Built in filters
Dictionary and distributed attack protection features
SMTP connection prioritization
SMTP AUTH
Logs
LDAP
eimsd
Things to watch out for when upgrading to EIMS 3.3
SMTP HELO/EHLO name used
EIMS 3.3 now uses the address name of a domain for the SMTP HELO/EHLO command and SMTP greetings. Check and make sure you don't have the address name of any of your domains set to an IP address. If it is, you should change the address name to be a domain alias that has an A record in the DNS that points to your server, then remove the IP address from your list of domain aliases.
SMTP connection reserves
EIMS 3.3 now has connection reserves to allow 3 level SMTP connection prioritization. The connection reserves default to 4 and 2, if you only have 4 or less SMTP connections configured in the Connection Settings, then nothing will be able to connect unless it is entered in the SMTP Host List. I recommend configuring EIMS with a minimum of 20 SMTP connections, this is what new installations of EIMS 3.3 default to. If you increase the number of reserved SMTP connections, check and make sure you have enough SMTP connections configured. The SMTP connection reserves are intended for prioritizing server to server SMTP traffic on port 25. While clients can continue to use port 25, they are often connecting from dynamic IP addresses which means their connections often can't be prioritized based on IP address. In EIMS 3.2 and later a second SMTP port on port 587 is available specifically for email clients to use, EIMS requires SMTP AUTH on this port so it can only be used by clients of your server. This allows clients uninterrupted access to your server for sending mail no matter how much load is on port 25. See Email client configuration for more information.
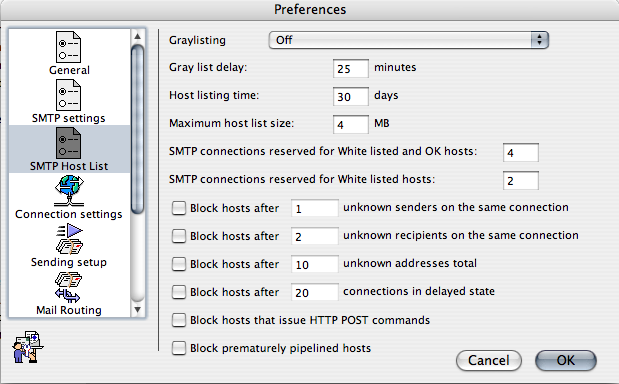
SMTP Host List
The SMTP Host List is a combined blacklist, graylist, and whitelist. If you do not wish to use graylisting or any of the other automatic features, the SMTP Host List can simply be used for manually blocking and whitelisting hosts. If you are upgrading from EIMS 3.2 or earlier, the SMTP Host List provides an enhanced and easier to use replacement for the IP Range Restrictions for SMTP and the DNS Filter Exclusions file. Hosts can be entered and changed manually, or automatically based on criteria set in the SMTP Host List preferences or by filter rules. Hosts in the SMTP Host List can have one of 5 states, Delayed, OK, Whitelist, Blacklist, or Block. The SMTP Host List also collects statistics on numbers of connections, messages, and unknown recipient requests from hosts. The "First seen" date will show as "New" when the "First seen" date and the "Last seen" date are the same.
You can manually add hosts and ranges by choosing Add from the Host List menu. You can also add or change the state of hosts by right clicking or control clicking on an entry in the Receive Error Log or a "from" entry in the Mail Log
To automatically add hosts to the SMTP Host List, choose one of the Graylisting settings in the SMTP Host List preferences. Monitor will add all hosts with a state of OK the first time they connect to your server. Options for only graylisting non-ESMTP hosts can be useful for minimizing delays to legitimate email while cutting down on spam from spambots, as most legitimate servers support ESMTP, while most spambots do not appear to do so.
The "Block hosts that issue HTTP POST commands" setting is for blocking open HTTP proxies that are being used to send spam.
The "Block prematurely pipelined hosts" setting blocks hosts that have sent more than just a HELO or EHLO command in their first lot of data. This is not compliant with the SMTP specifications, and is usually only done by spambots.
Host List states
Delayed: Hosts in the Delayed state will receive a temporary (450) response until they reach their "Listed until" time, after which they will switch to OK state the next time they connect. Any time a messages is delayed it is logged in the Receive Error Log.
OK: Hosts in the OK state have no special treatment other than to be allowed to use connections in the reserve for Whitelisted and OK hosts.
Whitelisted: Hosts in the Whitelisted state will only have the "Whitelisted host action" of filter rules applied to them, and are not blocked by the settings for HTTP POST commands, premature pipelining, or the limits on unknown recipients. Whitelisted hosts are also treated by filter plugins as a client that has used SMTP AUTH or is has been allowed to relay in the Relay Security settings, Filters such as the Short Host Filter, Sender Domain Filter, Strict Sender Domain Filter, No Message-ID Filter, and DNS blacklist filters do not check whitelisted hosts.
Blacklisted: Hosts in the Blacklisted state receive a permanent failure (550) response, and an error is logged in the Receive Error Log.
Blocked: Connections from hosts in the Blocked state are never accepted, much like the IP Range Restrictions for SMTP in EIMS 3.2 and earlier. The last seen time is updated whenever a blocked host tries to connect.
Listed Until time
If a host that is in Whitelisted, Blacklisted, or Blocked state connects, and it's "Listed until" time has passed, it will switch to Delayed if graylisting is on, otherwise it will switch to OK. Any time a host connects that is in a state other than Delayed, the "Listed until" time for that host is pushed forward if it is less than the time specified in the "Host listing time" preference. This results in a behavior where Whitelisted, Blacklisted, or Blocked hosts will stay in that state until no connections are seen from them for the "Host listing time".
Hosts remain in the SMTP Host List until they are manually deleted or the amount of memory needed for the SMTP Host List reaches the "Maximum host list size" setting. Once the maximum host list size is reached, hosts with the oldest "Last seen" time that do not have a "Listed until" date of Permanent will be removed to make room for new hosts.
Important:A "Listed until" time of Permanent does not do anything other than prevent the entry from expiring or being recycled. For example, it will not stop an entry with a status of OK from being blocked by a filter or other setting. Typically you would only set Blocked or Whitelisted entries to be Permanent.
Upgrading
When upgrading from EIMS 3.2 or earlier, the IP Range Restrictions for SMTP are automatically converted to entries in the SMTP Host List with a state of Blocked and a "Listed until" date of Permanent. If you use a DNS Filter Exclusions file under EIMS 3.2 or earlier, you can import it using the Import IP Ranges option under the Host List menu. Typically you would import the IPs with a state of Whitelisted, other states can be used if you wish to import lists of IP ranges for other purposes.
Built in filters
The built in filters can now be used to add and change rules on the fly from EIMS Admin.
The expression matching supports . to match any character, sets of characters in [] brackets, ? for an optional match, + and * to repeat matches, and a specified number of matches or a range of matches in {} brackets. ?, +, * and {} ranges are truly greedy, and will always match as many characters as they can. For example, .* will match all the characters, so should only be used at the end of an expression.
The filter rules also have the ability to change the state of hosts in the SMTP Host List for more effective trapping of hosts being used to send spam. Be aware that rules that automatically block or blacklist hosts could potentially be used as a denial of service if someone can maliciously trigger one from a host you wish to receive email from.
Filter actions
Refuse recipient: (RCPT TO filters only) recipient addresses matching the filter are refused. This does not necessarily stop messages if they are also addressed to other valid recipients.
Refuse message: (MAIL FROM and RCPT TO filters only) if the filter is hit, the message is refused, but subsequent messages on the connection will not be affected.
Refuse messages: if the filter is hit, all subsequent messages on the connection are refused.
Blacklist host: if the filter is hit, the host is changed to Blacklisted state in the SMTP Host List, causing any subsequent mail from that IP address to be refused.
Block host: if the filter is hit, the connection is dropped, and the host is changed to Block state in the SMTP Host List causing any subsequent connections from that IP to not be accepted.
The built in filter rules in EIMS 3.3 can completely replace the functionality of the following filters:
- Short Host Filter, use a rule of: HELO/EHLO does not contain "."
- Host Name Filter, Host Name & IP Filter, use a rule of: HELO/EHLO is <host.to.block>
- Recipient Filter, Spam Trap Filter, use a rule of: RCPT TO is <address@to.block>
- Route Address Filter, use rules of: RCPT TO contains "!", RCPT TO contains "%", RCPT TO starts with "@"
Some basic rules that are worth setting up on your server are ones to block HELO/EHLO names that are the IP address of your server, the host name of your server, and the domain name of your server. If you are handling multiple domains, add as many of these as necessary. These are safe to use as no legitimate host should ever be claiming that it's name is your IP, your server name, or your domain name. If you are running other services on the same computer that connect to EIMS using SMTP on port 25 (rather than port 587), you may need to Whitelist the IP of your server or the loopback address (127.0.0.1) in the SMTP Host List if they would hit these rules. When running other services on the same computer it is typically a good idea to whitelist them anyway.
Dictionary and distributed attack protection features
Graylisting goes a long way to slowing down dictionary attacks. This can be combined with other settings to block hosts due to bad behavior.
There are three settings to block on unknown addresses, which is what will typically occur with a dictionary attack, block on unknown senders on the same connection, block on unknown recipients on the same connection, and block on unknown addresses total. The unknown addresses total is the sum of both unknown senders and unknown recipients, and is listed in the SMTP Host List.
If a domain has forwarding for unknown users set to forward to an address, no recipient addresses in that domain will be considered to be unknown. Similarly, if the "Allow unknown MAIL FROM addresses" setting is on no sender addresses in that domain will be considered unknown.
The setting to block after too many connections in delayed state is useful for blocking hosts that connect to your server too rapidly, as can happen in a denial of service attack.
Hosts that have been Whitelisted in the SMTP Host List are not blocked by any of these settings.
SMTP connection prioritization
A distributed SMTP attack can result in all the available connections on an SMTP server being tied up, resulting in a denial of service that prevents legitimate mail from getting through. Denial of service may not be the intention of the attacker, these sorts of attacks have been seen where a spammer is simply trying to send a huge volumes of spam with no regard for the consequences this may have on the servers for the target domain. In order to minimize the impact of these sorts of attacks, EIMS 3.3 supports 3 level SMTP connection prioritization using the "SMTP connections reserved for Whitelisted and OK hosts" and "SMTP connections reserved for Whitelised hosts" settings. This can be used to prevent untrusted hosts from tying up all the SMTP connections on your server, assuring mail from Whitelisted hosts can always get through, and mail from OK hosts is more likely to get through. When the number of free SMTP connections reaches the "SMTP connections reserved for Whitelisted and OK hosts" setting, only connections from hosts in a Whitelisted or OK state in the SMTP Host List will be accepted. When the number of free SMTP connections reaches the "SMTP connections reserved for Whitelised hosts" setting, only connections from hosts in a Whitelisted state will be accepted.
For example, with the default settings of 16 SMTP connections, 4 reserved for Whitelisted and OK hosts, and 2 reserved for Whitelisted hosts, connections from Blacklisted or Delayed hosts, hosts that are not in the SMTP Host List, and hosts that are past their "listed until" time, will stop being accepted when 12 SMTP connections are in use (4 connections are available). If the number of connections in use reaches 14 (2 connections available), then only connections from whitelisted hosts will be accepted.
If you don't wish to use this feature, set both the connection reserve settings to zero.
It is a good idea to move clients to port 587 for sending mail via SMTP, that way they have their own separate pool of connections to use and will not be affected by a denial of service on port 25. See Email client configuration for more information.
SMTP AUTH
The "Require AUTH on SMTP Submit" setting should always be on. This setting defaults to on for EIMS 3.2.5 and later, it may have defaulted to off if your first version of EIMS was 3.2 to 3.2.4. This setting will probably be hard coded to be on and the checkbox removed in a future version of EIMS.
The "AUTH on SMTP" setting specifies how AUTH on port 25 should be handled.
Allowed This is the default setting, and is the same behavior as earlier versions of EIMS. Users can use SMTP AUTH to relay mail, but SMTP AUTH does not have to be used to receive mail for local users.
Disabled This setting prevents SMTP AUTH from being used on port 25. Typically you would use this when all your users are using the SMTP Submission port (port 587) and you don't want them to accidentally use port 25.
Required This setting requires that SMTP AUTH is used for all mail on port 25. Important: This setting will stop the outside world from sending you email, you should only use it if your server is behind a spam filter that is processing all your incoming mail and uses SMTP AUTH when forwarding it to EIMS.
Clients sending mail on port 25 that use SMTP AUTH bypass the Delayed and Blacklisted states in the SMTP Host List, and are not checked by MAIL FROM or RCPT TO filters. Clients using port 587 do not interact with the SMTP Host List or built in filtering.
Logs
Errors from the SMTP server, SMTP Host List, and built in filtering now go to the new Receive Error Log. This log has an extra field for the IP address of the remote host, and you can quickly change the state of that host in the SMTP Host List by right clicking or control clicking on an entry. You can also do this in the Mail Log, right clicking or control clicking on the "from" entry for a message will let you change the state of the host the message was received from.
Filter plugins will need rebuilt to log errors to the Receive Error Log.
LDAP
The LDAP server now supports spam firewalls/appliances checking for valid recipients via LDAP. LDAP queries for "email" objects, eg: email=user@domain, will return an "email" object if that address would be accepted as an SMTP RCPT TO recipient.
Images for users can now be served up via LDAP by putting a file named JPEGPhoto.jpg in to the users folder. The file must be 10KB or less in size.
eimsd
eimsd is a daemon version of EIMS Server. Under Mac OS X 10.4 and later the recommended way to run it is from launchd. See the man page for launchd.plist for an example launchd plist file, just remove the OnDemand key and change the strings in ProgramArguments array to the path to eimsd (which needs to be in your EIMS folder), and add any parameters you want to pass as extra strings. You can also run eimsd from Terminal for testing purposes. eimsd supports the following parameters:
- -d: daemonize, only needed for backwards compatibility with older OS versions or startup methods
- -p priority: run eimsd at the specified priority, only needed for backwards compatibility with older OS versions or startup methods, use the Nice key with launchd
- -u username: have eimsd switch to running under the specified username after binding TCP ports
- -g group: have eimsd switch to running under the specified group

Questions?
Features
Demo
Support
EIMS Quick Start
Email client configuration
EIMS 3.3 Documentation
Relay Security
OS 9 to OS X
Updates
EIMS mailing lists
Filters
Buy EIMS from Kagi
Last modified 23 February 2008. Copyright 1997-2008 Glenn Anderson.